Data purging is a key way to securely sanitize drives while avoiding e-waste. The new IEEE 2883 standards set out strict compliance criteria for purge, inspiring confidence in data center workers and ITAD vendors alike.
Data storage requirements are constantly increasing. And it’s no wonder. More data is being generated than ever before, and the rise in AI means that this data is increasingly useful and profitable.
One thing, however, hasn’t changed: the importance of responsible data management. When it comes to old drives, improperly sanitized hardware can jeopardize customer interests, brand reputation, and may even result in heavy fines. Data leaks pose serious risks, and sacrificing security means compromising safety.
Unfortunately, concerns over security are one of the major barriers to sustainable data storage, as companies large and small routinely opt to destroy, rather than reuse, old devices. These habits may be hard to break, but the message should be simple: make it crystal clear that one can often securely purge data from storage devices without physically destroying the storage media. And this is where the guidance on data purging in the IEEE 2883 standard comes in.
Improvement Over Older Standards
Despite its crucial role in data security and sustainability, data purging often faces communication hurdles. Older standards suffer from vagueness, and a lack of clear guidelines can lead to confusion, e-waste, and even data leaks. Thankfully, the new IEEE 2883 standard provides a comprehensive framework for data purging. This standard rigorously defines terms and details how techniques vary across different types of media and interface.
Compared to the older NIST 800-88 (2014) standards, the IEEE 2883 standard (2022) represent a substantial improvement. It offers strict compliance conditions, unlike NIST’s general guidelines. Plus, even though both the National Institute of Standards and Technology (NIST) and the Institute of Electrical and Electronics Engineers (IEEE) are highly credible organizations, IEEE is a global organization with members and activities worldwide ensuring broader applicability and acceptance of its standards.
IEEE 2883 also explains how to talk clearly about data sanitization. It replaces vague terms like “Wipe”, “Delete”, and “Data Destruction” with the more specific “Clear”, “Purge”, and “Destruct.”
In a recent SERI podcast (Sustainable Electronics Recycling International), industry expert Jonmichael Hands emphasized the importance of using language precisely. We need to be “diligent in using the right terminology and to stop saying we’re going to ‘wipe’ the drives”, Hands explains. He added that loose phrasing has “caused a lot of uncertainty for end customers, which leads to shredding”.

Related Reading
IEEE 2883 covers a lot more than just data purging. To learn how the new standard differs from NIST 800-88, check out our breakdown.
NIST is especially behind-the-times when it comes to NVMe/PCIe interfaces. The first NVMe drives came out in 2014. Since this was the same year NIST 800-88r1 was written, that standard was published before many of the NVME sanitization commands were written. That’s a problem, since NVMe devices now constitute the vast majority of enterprise flash.
By contrast, IEEE 2883, released in 2022, contains extensive requirements for NVMe device sanitization. “Conveniently the folks that wrote the NVMe spec, SAS spec, [and] SATA spec for sanitize command were also the authors of 2883,” says Hands. “So don’t worry: this lines up very very clearly with those specifications when you’re sending the sanitize command through the storage interface.”
The Importance of Data Purging
Let’s consider definitions: IEEE 2883 defines “sanitize” as “rendering access to target data on storage media infeasible for a given level of effort.” While absolute zero-risk data security is impossible, digital security revolves around rendering access infeasible.
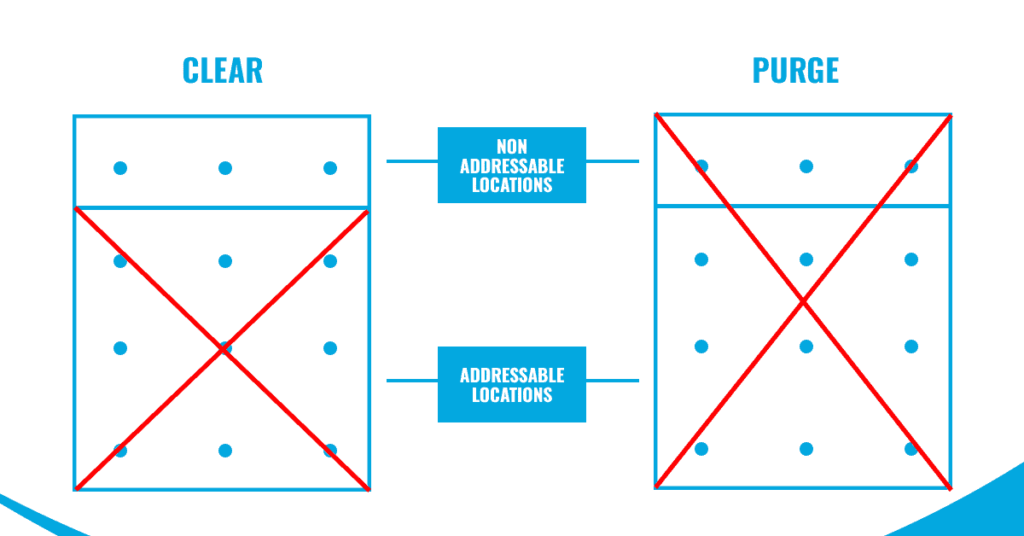
Under IEEE 2883, there are three disposal categories: Destruct, Clear, and Purge. While Destruct physically destroys storage media, Clear and Purge employ logical techniques to make data inaccessible.
The difference between Clear and Purge lies in their effectiveness against different data recovery techniques. Clear works against “simple non-invasive data recovery techniques” while Purge works against “state-of-the-art laboratory techniques.”
Purge is crucial to the advancement of sustainable storage. It offers enhanced security, while also often allowing for drive reuse. Even degaussing, which renders the device’s firmware inoperable along with the rest of the data, allows for the extraction of useful hardware components, potentially reducing e-waste and mitigating environmental impact.
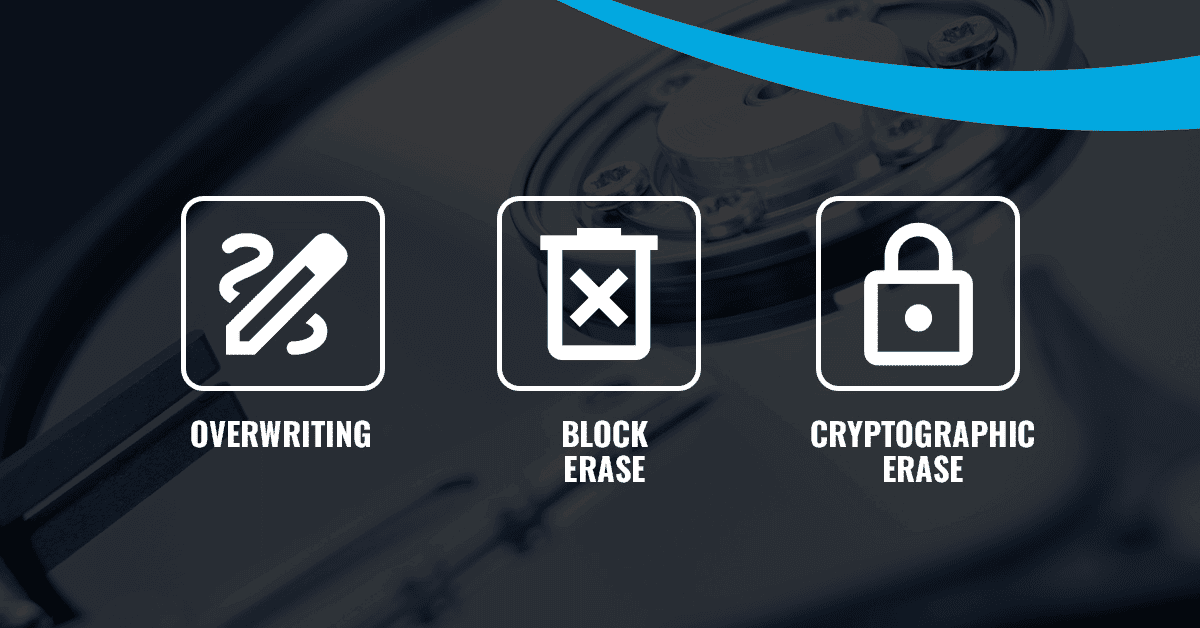
Three Methods For Data Purging
There are three main purge methods: Overwrite, Block Erase, and Cryptographic Erase.

Overwrite: This method writes over existing data with a specific pattern, rendering it unrecoverable. Used properly, a single overwrite is typically sufficient to render data recovery infeasible. Overwrite is applicable to most electronic storage media types. However, it can be time-consuming. For Purge Overwrite (as opposed to Clear Overwrite), you need to issue the overwrite instruction via a device command.
Block Erase: This involves electrically erasing every block in the drive. Primarily used for semiconductor media like NAND flash, this method is faster than overwrite but still time-consuming. It involves issuing a command via the host interface.
Media-based Cryptographic Erase: This technique involves changing and deleting the encryption key, making data permanently indecipherable in the blink of an eye. While exceptionally fast, it doesn’t apply to certain media types where encryption keys aren’t stored within the media, such as encrypted LTO-4 tapes. IEEE 2883 also specifies the required strength of the cryptographic algorithms and keys involved.
How Data Purge Methods Vary
Storage media types include HDD and SSD, of course, as well as less common devices, such as tape storage and optical storage. Regarding interfaces, the three main categories are ATA (including SATA, PATA, etc.), SCSI (including SAS, USB, and Firewire), and NVMe (including PCIe). The specific commands used for data purging vary depending on the media type and interface.
For example, cryptographic erase is sometimes available for HDDs, but not always. HDDs typically use specific commands based on their interface (usually SATA or SAS). Jonmichael Hands highlights the significant time difference between Overwrite and Cryptographic Erase for HDDs. “Where an overwrite of a modern hard drive may take 20 or 30 hours, you can do a crypto erase in about one or two seconds”, he explains.
Additionally, a fourth method, degaussing, is available for HDDs. This involves exposing the media to a strong magnetic field, effectively erasing all data. Degaussing is generally deployed for damaged or inoperable media, as it typically renders the drive unusable. IEEE also provides specific degaussing instructions for other media types, such as floppy disks.
Additional Tips for Data Purging
The full IEEE 2883 report is worth a read. It’s written with clarity in mind, and contains detailed explanations, aimed at the non-expert, of the types of sanitization at play. Here are some additional tips that we’ve found with regard to Purge:
- Match: Aligning the data purge method with the media type is crucial.
- Don’t Mix: Mixing different purge methods may impede verification and increase processing time, especially for cryptographic erasure.
- Avoid: It’s advised to avoid cryptographic erase if your device is only partially encrypted, or if you believe sensitive data may have been added to the device before encryption was enabled.
- Choose: Select appropriate purge software. Consider ADISA’s ranking, which is based on three threat levels. Also, be wary of software that offers an excessive number of algorithms or passes.
- Document: Compliance certificates are not included in the IEEE 2883 standard but can be found in ISO 27040-2023.
It’s also worth paying special attention to verification, the process by which you ensure that data has been completely purged from the storage device. According to IEEE 2883, it is necessary to confirm that the correct command was executed, rather than verifying whether the command functioned as required. If your chosen method was Cryptographic Erase or Block Erase, it is crucial to ascertain that the data was effectively scrambled and rendered unreadable. If readable portions are found, resort to destruct methods for further data sanitization.
Again, details vary depending on the type of device and interface in question. When in doubt, check the standard!
Secure And Sustainable
IEEE 2883’s emphasis on rigorous data purging methods are a crucial part of its goal to make sanitization more secure and sustainable. Industry experts agree that IEEE 2883 is the future of data purging. As Steve Mellings, CEO of ADISA, puts it, “We really need to get behind IEEE 2883 as a sanitization specification because it really is the best that there’s been. That’s without a shadow of a doubt in my opinion.”
In sum, the new IEEE standard brings both clarity and detail to the data purging process. It specifies specific purge methods by storage interface, removes vagueness with carefully chosen terminology, and provides clear compliance conditions rather than general guidelines. In doing so, it empowers ITAD firms that wish to ensure a clear and secure process for data purging. But it’s more than that: it also trumpets the message to data center managers everywhere that secure disposal can be done in a sustainable way. And that’s good for drives, good for the bottom line, and good for the planet.
Secure sanitization requires the right commands, but also an air-tight workflow. Get in touch with Horizon for expert support with every aspect of data sanitization.