The IEEE 2883 standard is highlighting non-destructive methods of data sanitization, paving the way for greener hardware lifecycles.
When it comes to sustainable business, no firm is an island. Greening the tech industry will require massive coordination between businesses.
A major part of this coordination is careful standards work governing each stage of an asset’s lifecycle. Well designed standards interlock, allowing circular practices to be built up brick by brick from complementary guidelines.
IEEE 2883-2022 is a new standard which clarifies data sanitization methods and terminology. Notably, it communicates how devices can be securely wiped without resorting to physical destruction. As such, this new standard, while narrow in scope, is a crucial piece of the overall circularity puzzle.
Strategic Standards for Sustainable Technology
Making tech greener, and reducing e-waste, is a massive undertaking. To make progress, one must break the goal down into smaller and actionable sub-goals.
E-waste accounts for only 2% of solid waste streams, but makes up 70% of hazardous waste within landfills!
The Circularity Electronics Partnership has released a roadmap detailing what changes are necessary to create an economically viable circular industry. The roadmap draws on the knowledge of 80 experts from 40 companies, including Dell, Amazon, Google, and Microsoft.
While quite general, the CEP roadmap is a useful framework to see precisely how sanitization standards fit into an overall strategy for greening the tech industry.
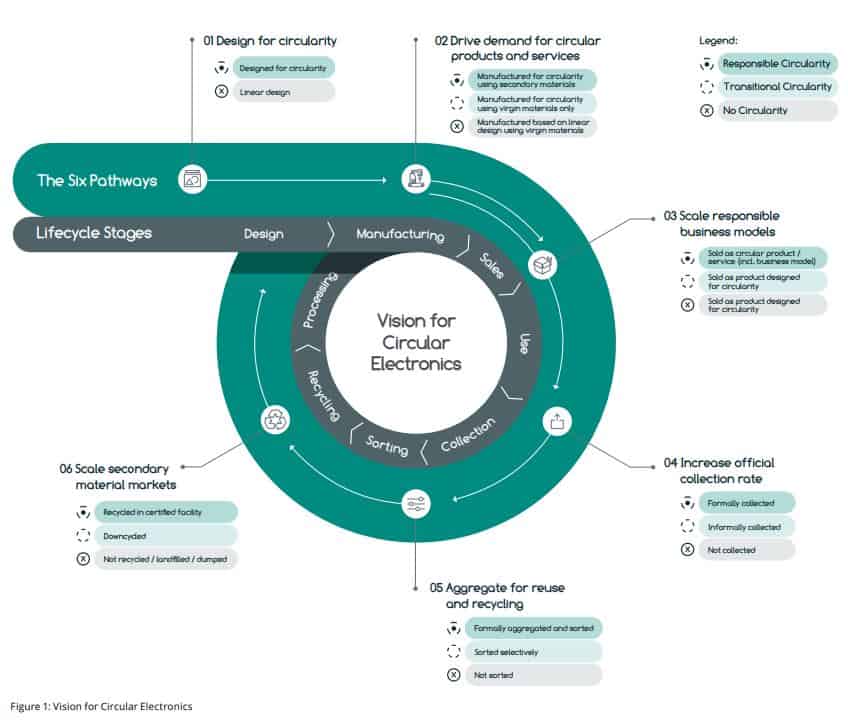
As per the graphic, the roadmap is based on six “pathways”. Each pathway aligns with different stages in the lifecycle of electronic assets. For every pathway, the report details what action is needed, what previous actions it depends upon, and which actors can best create the change.
Pathway three is to scale responsible business models, and standards work is crucial here. One key action in pathway 3 is the creation of global best practices on data sanitization. As the report puts it, “Clear communication about the available data sanitization options can promote their use and reduce insecurities.”
Clearly, this involves standards such as the IEEE 2883. These practices are a good starting point for encouraging circularity, as it has no prerequisites other than careful research.
IEEE Standards: Some Background
IEEE is the Institute of Electrical and Electronics Engineers. Its Standards Association is heavily involved in the creation of new standards for everything from sanitization, to nanotechnology, to AI.
IEEE has been in the standards game a long time. While the organization was formed in 1963, one of its parent organizations, the American Association of Electrical Engineers, was doing standards work all the way back in 1884!
Because storage technology changes rapidly over time, it’s important to keep data sanitization standards up to date. Unfortunately, according to Fredrik Forslund, Director of the International Data Sanitization Consortium, the creation of new storage devices is outpacing current standards.
“While data storage technologies change significantly around every 18 months, globally referenced guidelines, best practices, and standards may take years to revise,” Forslund explains.
Thankfully, one of the perks of IEEE is that the organization’s size and resources mean that they can update standards more regularly.
Regulation and Communication
A criterion for compliance is only useful if the standard communicates it clearly, with vagueness removed.
Here are just a few examples of places where IEEE 2883 aims to be clearer than previous standards:
- Explicitly addressing new devices. Older standards may leave it unclear if the sanitization process for a new device is in conformance.
- Tidying terminology. In old standards, “delete” is sometimes used to refer to actual removal of data, and sometimes to refer to deletion of file system pointers. “Data shredding” sometimes refers to physical shredding, and sometimes to deleting an encryption key. IEEE 2883 will help to remove such ambiguities.
- Sorting out the clear/purge/destruct categories. NIST 800-88, created in 2006, makes a distinction between “NIST Clear” and “NIST Purge”, which defend against keyboard and laboratory attacks respectively. But as technology develops, this distinction becomes less straightforward.

But there’s more to communication than clarity: there’s also framing to consider. From a narrative standpoint, IEEE 2883 is a clarion call against unnecessary e-waste. “Companies should prioritize the purge sanitization method over the destruct sanitization method for most data and work with their vendors to qualify and verify the purge sanitization method”, insists the standard.
The next generation of sanitization standards needs to define its terms, better specify compliance, and above all send a message about how responsible sanitization ought to work. It’s precisely these goals which IEEE 2883 is crafted to meet.
IEEE 2883: Infeasible Retrieval and Circularity
Precisely what does it mean to sanitize a device, anyway? The standard defines “sanitization” in the usual way, as “the ability to render access to target data on storage media infeasible for a given level of effort”.
“Infeasible” is an important qualifier. Data doesn’t need to be impossible to access in order to be secure. After all, lots of unlikely things are possible. It’s possible someone could successfully guess all of your bank account passwords, but such guesswork is an infeasible strategy, and almost certain to fail.
Here, the success of IEEE’s framing depends on the gritty details. The standard must describe purge methods which meet high standards of security, making “recovery of target data infeasible using state-of-the-art laboratory techniques” while also preserving the storage media and the storage device in a potentially reusable state.
The Three Methods
IEEE 2883 aims to be crystal clear about the relation between three categories of sanitization: Clear, Purge, and Destruct.

“Destruct” is when a device is melted, incinerated, disintegrated, or otherwise physically destroyed. The previously acceptable methods of shredding and pulverizing drives are no longer approved sanitization techniques. “Clear” is using “logical techniques on user data on all addressable storage locations” to prevent simple recovery.
“Purge” is the most interesting category. It makes recovery of any data, including data on reallocated sectors, infeasible, while still allowing drive reuse. The emphasis on reallocated sectors is important, because data residing on unaddressable locations can still be accessed using laboratory techniques.
In an overview of IEEE 2883, storage veterans Tom Coughlin and Jonmichael Hands describe purge as “the most important sanitization method for enabling circularity for storage devices.” The hope is that by outlining rigorous standards for what counts as a successful purge, companies will trust it as a greener alternative to destruction.
Purge Processes
Multiple erasure and encryption processes can be used in purge. These processes are:
- Cryptographic Erase: This changes the encryption key in the blink of an eye.
- Overwrite: Overwrites all data with certain special patterns which can later be verified.
- Block Erase: This zeroes out erase blocks in SSDs.
“We understand this encryption technology, we use it and trust it across all the devices across all the data centers on the planet today. So we can use that same technology to basically render all of the data on the drive inaccessible.”
Jonmichael Hands, advisory member of the Circular Drive Initiative
The standard goes on to explain in detail just how sanitization methods should vary by media (HDD, SSD, Optical, etc) and interface (SATA, SAS, NVMe). For example, methods 1 and 3 may be jointly used on SSDs, whereas method 2 is good for certain HDDs (though it takes about one hour per TB).
Ultimately, the choice of sanitization technique “depends on the owner of the data, the storage media, and the organizational security policy to be enforced.” The category selected also depends on the task at hand. “Some security policies may require clear, whereas others may require purge or destruct.”
Strength in Numbers: Interlocking Standards
The art of standard creation is fashioning guidelines to fit with neighboring standards.
IEEE 2883 is written so that it can be easily referenced by future versions of NIST or ISO (International Standards Organization) guidelines. While compatible with future standards, it sometimes refers back to old ones. Sanitize Purge Cryptographic Erase, for instance, looks back to AES256, an encryption standard developed by NIST.
Guidelines can also complement one another, bringing modularity to standards development. This is good, because while IEEE 2883 is very detailed on how one should sanitize different devices, it doesn’t say much about when.
The when of sanitization is left to an update to the ISO/IEC 27040 standard. This standard specifies when in an asset’s lifecycle it should be sanitized, and how one should verify and document this sanitization. While the 2015 version of ISO/IEC 27040 was aligned with NIST standards, the new version is aligned with IEEE 2883.
The ISO/IEC 27040 update is also more “system-centric” in flavor than its 2015 version, with device-specific language removed. This is to keep pace with current technology, as cloud storage is far more prevalent than it once was.
Creating Circularity Link by Link
Sustainable, economically viable business practices don’t emerge in a vacuum. They take a lot of forethought and careful groundwork. Standards are a huge part of this, and form an essential preliminary for the greening of technology.
What’s more, these standards work in concert. Each links to others, sharing definitions and complementary criteria for compliance. IEEE 2883 looks back to older encryption standards, forward to new NIST standards, and complements current standards such as the ISO/IEC 27040 update.
Ultimately, IEEE 2883 is about more than just security: it’s about communication. To promote reuse and avoid e-waste, it needs to be said loud and clear: data is safe if it’s infeasible to recover, and attaining this infeasibility doesn’t require physical destruction.
Find out how Horizon can help you manage your hardware lifecycles to reduce total cost of ownership and green your business.











