New advancements in storage technology mean new challenges for data sanitization. In the face of a changing landscape for storage media, the IEEE 2883 standard gives forward-thinking guidance on the matter. Released in 2022, it clarifies terminology to remedy confusion surrounding the sanitization of logical and physical media, and sets out the distinction between Clear, Purge, and Destruct methods of sanitization.
Standards are never just standards: they’re about communication as much as regulation. By getting the message out that non-destructive sanitization methods are secure and effective, IEEE 2883 aims to promote circularity in data storage. So far so good: it’s already making a buzz with storage experts, leading to further awareness of the issues it addresses. The impact of the standard is additionally boosted by organizations that are making IEEE 2883 a key part of their policies.
Read on to learn about IEEE 2883 and how it continues to make a deep impact on circularity practices.
Why is IEEE 2883 So Important?
IEEE 2883 is most directly concerned with preventing data from getting accessed from improperly sanitized drives. However, it also plays a key role in a fight against the scourge of electronic waste, or “e-waste”.
E-waste has become the fastest growing waste stream in the world. From 2019 to 2022, it spiked from 53 million tons to 62 million tons. While e-waste only represents 2% of solid waste streams, it makes up 70% of hazardous waste in landfills. Such waste has serious downsides, and has been linked to everything from soil and water contamination, adverse neonatal outcomes, as well as negative impacts in neurodevelopment and respiratory function in children. These adverse affects can be indirectly mitigated, at least in part, with savvy regulation.
The Institute of Electrical and Electronics Engineers, or IEEE, was formed in 1963, although one of its parent organizations has been into standards creation work since 1884. With collaborations spanning 160 countries, IEEE is an organization with the scale and scope to keep up with the challenges that the rapid evolution of technology brings along.
The IEEE 2883 data sanitization standard is for industry regulation, but also for communication. Since drives end up getting destroyed mainly due to security reasons, fighting myths about sanitization is particularly useful in discouraging the unnecessary physical destruction that fuels e-waste.
To accomplish this, IEEE 2883 clearly communicates the compliance criteria, without using vague terminology. This has led industry experts to adopt and boost its clarion call. Storage gurus are already discussing the IEEE standard in podcasts, papers, and conference talks. Organizations such as the Circular Drive Initiative are pushing for wide adoption of IEEE 2883 as an economically robust and environmentally viable standard.
Another feature of IEEE 2883 is that it interlocks with other standards, facilitating continuity and easing compliance. For instance, the 2014 version of ISO/IEC 27040 was aligned with NIST 800-88, while its latest version aligns with IEEE 2883. Meanwhile, ADISA, a global certification body that promotes best practices in data sanitization, updated its sanitization certification to cohere with IEEE 2883.

Related Reading
IEEE 2883 is more than just a standard. It’s a piece of careful communication which will form a key part of circularity frameworks moving forward.
The Three Sanitization Methods
The three main sanitization methods discussed in the IEEE 2883 are Clear, Purge, and Destruct. Briefly, Clear protects against non-invasive data recovery while Purge works against state-of-the-art data recovery techniques. Both Clear and Purge are non-destructive, while the third method, Destruct, physically renders data unretrievable, generating e-waste in the process.

Clear
The Clear method of sanitization given in the IEEE 2883 is mainly suited for routine data erasure. It erases data from all addressable locations while keeping the drive usable. A simple and cost effective method particularly suitable for low sensitive data, Clear offers effective protection against non-invasive data recovery carried out within the host interface.
Clear Overwrite and Clear Block Erase are the two techniques by which Clear sanitization can be carried out. In the Overwrite technique, every addressable location is overwritten with data patterns via a host command. Block Erase, which is mainly applicable to SSDs, erases data a block at a time. Compared to Overwrite, Block Erase is much quicker, though block erasing a large storage device may still be time consuming.
However, the IEEE definition of “Clear” has come under criticism in some quarters for being, well, unclear. In research for ADISA, technology director Phillip Turner points out that the new standard does not precisely define “user addressable location.” This further highlights the difficulty in attaining precision in sanitization standards, failing which the recycling decisions can get disrupted, compounding the e-waste problem.

Related Reading
To get clear about Clear, and understand how it differs from Purge, check out our handy guide.
Purge
The Purge sanitization method, like Clear, also uses logical techniques. It has the potential to retain drive reusability, but is still a suitable method for cases where enhanced security is needed. While Clear is effective against simple non-invasive data recovery techniques, Purge renders data inaccessible against even state-of-the-art laboratory techniques. This is achieved by sanitizing data in both addressable and non-addressable locations.
There are three techniques to purge a drive: Purge Overwrite, Purge Block Erase, and Purge Cryptographic Erase. As in Clear, the Overwrite technique involves writing over existing data with a specific pattern. Unlike Clear Overwrite, the Purge Overwrite command is given via a device command, rather than through a host interface. Block Erase, on the other hand, electrically erases all the blocks in the drive. The third and the fastest of the Purge technique, Cryptographic Erase, makes data undecipherable by securely deleting the encryption key.
A fourth technique, degaussing, sits uniquely between Purge and Destruct. A “degausser” is a device that uses a strong magnet to effectively erase data. In most cases, degaussing a drive makes it unusable. However, the drive is left physically intact, allowing value recovery of rare components. However, there’s a risk of incomplete data erasure if the magnet in the degausser isn’t sufficiently strong. This is one reason it is not listed as an accepted purge technique in IEEE 2883.

Related Reading
Purge methods are key to data center sustainability. They provide secure sanitization for storage devices, while also allowing for the possibility of reuse and component extraction.
Destruct
The third method of data sanitization in IEEE 2883, Destruct, permanently renders data inaccessible and the drive unusable. Among the three methods, Destruct is the most labor intensive and also results in e-waste. While Purge and Clear methods are ideal from a sustainability standpoint, Destruct can be necessary in cases of extraordinarily sensitive data or when Purge or Clear verifications fail.
The explosive increase in demand for storage media makes drive reuse a significant part of addressing e-waste problems. But due to data security concerns, most drives are still destroyed. This adds to the sharp rise in e-waste generation. According to the Global E-waste Monitor, e-waste is projected to rise 2.6 million tons annually, reaching 82 million tons by 2030.
IEEE 2883 approves three destruction techniques: Incinerate, Melt, Disintegrate.
In a departure from early standards such as NIST 800-88, IEEE 2883 doesn’t include shredding and pulverizing as accepted techniques. While shredding is, anecdotally, still the most common method of destroying hard drives, a point of concern is the risk of retrieving data from shredded pieces of platter. After all, as the areal density of magnetic media increases, more and more data can fit on such minute shreds. This is also part of the reason why shred and pulverize have been dropped from the latest IEEE 2883 standard.
In a discussion on the Sustainable Electronics Podcast, industry expert Jonmichael Hands raised the issue of data retrieval from leftover shreds of densely written drives. But founder and CEO of ADISA, Steve Mellings, counters that this isn’t a major problem if care is taken in disposing the scraps properly. Whoever is right, this much remains common ground: a tight workflow is essential for secure destruction.

Related Reading
Drive destruction, while sometimes necessary, is overused. That’s a problem, since destroyed drives are a major source of e-waste.
What Else Needs to be Done?
In addition to developing up-to-date, robust, and clearly drafted standards, there is much to do to further sanitization and circularity goals. To this end, UK circularity leader Richard Kenny and his fellow members at Circular Drive Initiative (CDI) are working to develop a grading system to categorize reusable drives. The recertified drives will be graded based on use cases and device health.
The grading system is still under development, but would work roughly as follows:
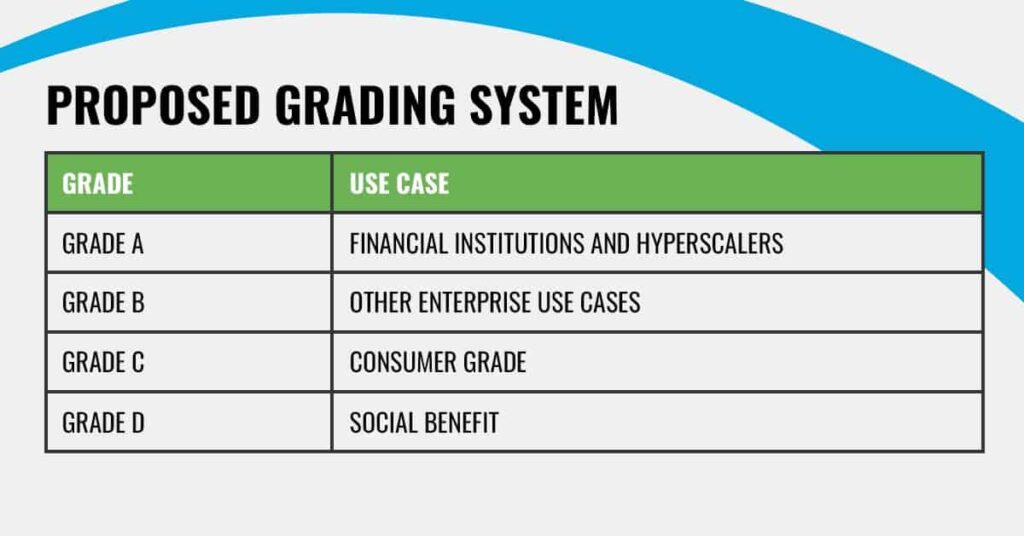
Grade A drives would be reserved for players requiring high-sensitivity. Less sensitive use cases in the enterprise, such as day-to-day storage used by employees of medium/small businesses, would use Grade B drives. Grade C drives are potentially consumer grade, although the consumer may need to back up data to be safe (which is best practice in any case). Finally, Grade D drives are appropriate for social benefit and charity, but mostly unsuitable for critical company systems.
This grading system would be hugely helpful. In a recent paper, Kenny and Jonmichael Hands point out that when drives are securely wiped, metrics for health and quality still have high variance. Given this lingering uncertainty, grading drives would give a clearer picture of the appropriate use-case for a sanitized drive.

Related Reading
Decisions about whether to utilize reused drives are ipso-facto decisions about whether to purchase new devices. What you decide impacts both the environment and your wallet.
Is Less More? Hard Drive Procurement and the Waste Hierarchy
Reuse is all the more important given that e-waste recycling at scale, particularly for storage media, hasn’t materialized. Despite the broad consensus on the benefits of recycling the percentage of e-waste documented as properly collected and recycled was less than 22.3% in 2022. Worryingly, this is projected to drop to 20% by 2030. This further indicates the need for better communication and collaboration around standards like IEEE 2883.
Related Reading
Most drives are destroyed, and most destroyed drives aren’t recycled. When it comes to encouraging a circular economy, finding ways to drive home the importance of reuse is key.
The Future of Data Sanitization
IEEE 2883 is key to addressing data security concerns that form a barrier to sustainable derive sanitization, fueling e-waste via unnecessary destruction. The standard clarifies the three sanitization methods, lists acceptable techniques, and discusses the varying levels of security and environmental impact of each. Clear offers basic security and ease, Purge offers enhanced security with possible reusability, and Destruct offers high security but with no reusability and serious environmental costs.
By providing a focal point around which messaging, collaboration, and other regulations revolve, standards like IEEE 2883 are central for achieving data security goals and promoting circularity practices. It provides a direction in the face of challenges inherent to data sanitization, acting as a foundation for future standards. Moving forward, its emphasis on clarity will act as a tool for better communication, deeper understanding, and increased adoption of good data management practices, helping minimize global e-waste.
Reach out to see how Horizon can help you procure drives, sanitize media, or plan a hardware refresh.











