The growing e-waste crisis has sparked a gradual shift in how used drives are dealt with. Instead of simply destroying drives, the focus is moving towards “purge and reuse”, where data is securely wiped and the storage device gets a second life. However, drive destruction is sometimes still necessary. This may be because a drive failed a purge verification or because the data in question is highly sensitive.
Whatever the reason, drive destruction should be carried out in the most secure manner possible. But as drive technology evolves, so too do the most secure methods for destruction. The approved methods specified in the new IEEE 2883 differ from those in the older NIST 800-88, with shredding and pulverizing now discouraged for security reasons.
These changes underscore an evolving landscape where technology and environmental concerns go hand-in-hand. Ultimately, responsible drive destruction requires a balanced and conscientious approach that considers both environmental sustainability and data security.
Hard Drive Destruction In NIST 800-88
Before addressing the latest and greatest destruction advice, it’s worth seeing why older standards leave something to be desired.
The NIST 800-88 standard, last updated in 2015, uses ambiguous terminology. According to NIST 800-88, the term “Destroy” is defined as follows:
“Destroy renders Target Data recovery infeasible using state of the art laboratory
NIST SP 800-88r1, §2.5
techniques and results in the subsequent inability to use the media for storage of data.”
However, the standard’s definition of ‘purge’ is similar – too similar, in fact. As defined in NIST, “Purge applies physical or logical techniques that render Target Data recovery infeasible using state-of-the-art laboratory techniques”.
Since it isn’t explicitly stated that purge must leave drives potentially reusable, the NIST definitions for ‘Destroy’ and ‘Purge’ overlap. For instance, incineration, a destruction method, also aligns with the definition of purge.
To make a long story short, this makes it so every destruction method is also a purge method, as the standard itself acknowledges:
Destructive techniques also render the device Purged when effectively applied to the appropriate media type, including incineration, shredding, disintegrating, degaussing, and pulverizing.
NIST SP 800-88r1, table 5-1

Related Reading
The new IEEE 2883 standard has a lot to say, and not just about drive destruction. It also give detailed instructions, by media type, for purging storage devices.
NIST 800-88 lists a range of destruction techniques, including shredding, pulverizing, disintegrating, and melting. It also acknowledges the effectiveness of degaussing in specific cases. But in the face of muddled definitions, one wants a clearer distinction between purge and destruct.

Moreover, NIST’s guidance for SATA, SCSI, and Flash drives raises concerns. The recommendation is to “Shred, Disintegrate, Pulverize, or Incinerate by burning the device in a licensed incinerator.” This prioritizes destroying potentially recyclable drives over recovering valuable components, further amplifying the need for better clarity and a more environmentally conscious approach.
Evolving Challenges in Hard Drive Destruction
The landscape of data destruction faces new challenges, particularly as drives continue to increase in density. As more data can now fit on smaller fragments left after shredding, concerns about data security escalate. The NIST 800-88 standards address this worry in passing, although it ultimately lists shredding and pulverization as accepted techniques.
Applying destructive techniques to electronic storage media (e.g., flash memory) is also becoming more challenging, as the necessary particle size for commonly applied grinding techniques goes down proportionally to any increases in flash memory storage density. Flash memory chips already present challenges with occasional damage to grinders due to the hardness of the component materials, and this problem will get worse as grinders attempt to grind the chips into even smaller pieces.
NIST SP 800-88r1, §2.4
Industry expert Jonmichael Hands highlights the severity of this threat. “If you just try to break a hard drive, you have little tiny shreds that are three or four millimeters. That’s a problem now. It didn’t used to be”, Hands explains. He points out that some new drives can contain as much as 2.4 TB of data per disk platter, with over 500,000 tracks per square inch. “I don’t think people quite have a grasp on just how dense data is.”

Related Reading
Heat-Assisted Magnetic Recording, or HAMR, has resulted in the densest hard drives yet. Areal density will continue to increase in the years ahead.
In contrast, Steve Mellings, CEO of ADISA, isn’t quite as concerned about the potential risk of shredded drives. He points out that shredded remains are often piled together and stored in a secure location. Additionally, he suggests that attention would be better directed towards ensuring that drives are transported securely.
I think if a threat adversary who had that type of technical capability and motivation was looking to attack the ITAD sector, I don’t think it would be at the shredded particle size because their likelihood of successful attack is so low. It would probably be closer to the client on a vehicle just leaving the facility where the drives may still be intact
Steve Mellings, CEO of ADISA.
The different perspectives here highlight debates around what part of the destruction process should be emphasized. Should the focus be on the methods themselves, or on secure storage and chain of custody? There’s a third option, of course: both!
Advancements in Data Destruction: IEEE 2883 Standards
The IEEE 2883-2022 standards bring a much-needed clarity to ‘destruct’ and ‘purge’. ‘Destruct’ is defined much as before, but the changed definition of ‘purge’ gets rid of the overlap.
Destruct: Sanitize using physical techniques that make recovery of target data infeasible using state-of-the-art laboratory techniques and results in the subsequent inability to use the storage media for storage.
Definition of ‘Destruct’, IEEE 2883, §3.1.
Purge: Sanitize using logical techniques or physical techniques that make recovery of target data infeasible using state-of-the-art laboratory techniques, but that preserves the storage media and the storage device in a potentially reusable state.
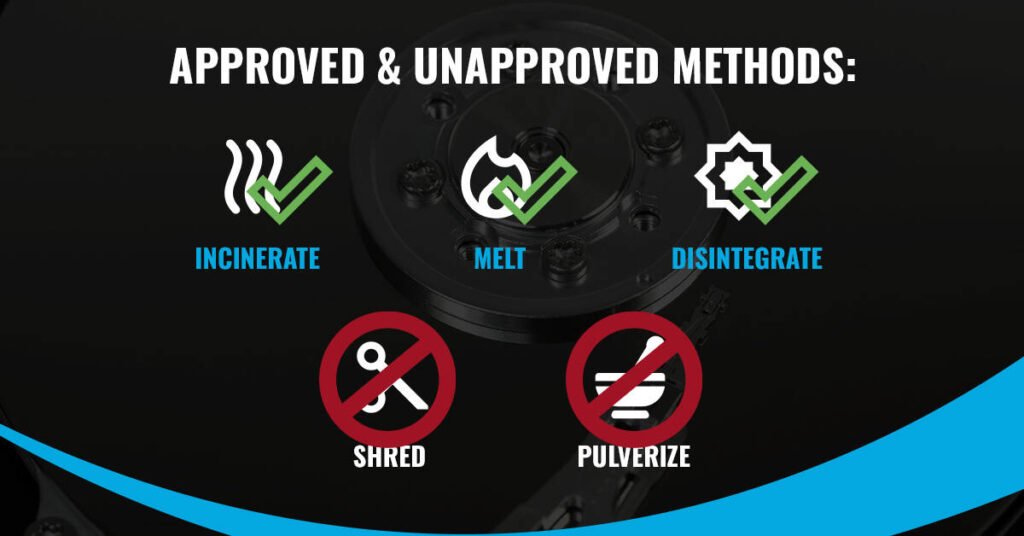
IEEE 2883 also updates the list of accepted destruction methods. Shredding and pulverizing are no longer approved methods, leaving disintegration, incineration, and melting.
IEEE 2883 is more than just a set of disposal specs, however. It clearly communicates the importance of environmentally responsible disposal. Here are some key points:
- Among clear, purge, and destruct, IEEE 2883 identifies destruct as the most labor-intensive disposal method, due to the specialized equipment involved.
- IEEE 2883 advises companies to prioritize purge sanitization methods and work with their vendors to verify that method resulted in a successful wipe.
- Crucially, the standards acknowledge that destruct methods generate e-waste, resulting in hazardous material like toxic dust or combustion products.
- The standards emphasize that shredding and pulverization are obsolete.
- IEEE 2883 recommends the use of destruct methods only for handling extremely sensitive information or instances where a purged drive fails the verification process.
These nuanced guidelines reflect a comprehensive and forward-thinking approach to data destruction, one which considers both security and environmental implications.

Related Reading
IEEE 2883 is raising the bar for secure and eco-conscious ITAD practices. See our full breakdown below.
Understanding Degaussing in Data Destruction
While IEEE 2883 makes the boundary between ‘destruct’ and ‘purge’ a lot clearer, degaussing remains a special case.
When you degauss a drive, a powerful magnet renders magnetic media, such as a hard drive or floppy drive, unreadable. It can erase firmware, rendering a drive unusable. So maybe it’s a destruct method, like incineration or melting. But it also leaves some components, such as rare earth magnets, intact. So maybe it’s actually a purge method, like overwrite or cryptographic erase. Which is it exactly?
Degaussing occupies a unique position in the realm of drive disposal, because its effectiveness depends on the strength of the employed magnet. A weak magnet might leave data recoverable, while a sufficiently strong one renders the drive unusable. As the magnetic coercivity of hard drive platters increases, progressively stronger magnets become necessary—a challenge that NIST standards had foreseen.
Why? It’s all about the size of the magnetic grains, says the magnetic materials group, based at the University of Birmingham. “Smaller particle size and higher magnetization lead to better quality recording, i.e. greater signal to noise ratio”, they explain. Magnetic coercivity is a key part of this drive for density. “As the density of recording increases then the magnetic domain size decreases and so the particle size must decrease and the coercivity of the material must increase.”
Accordingly, the IEEE 2883 states that degaussing is only deemed appropriate when strict documentation procedures are followed and vendor-approved tools are used. The standard cautions that some magnets might lack the requisite strength for effective degaussing. As with anything related to data security, there’s a need to adhere precisely to recommended practices.
Responsible Data Destruction
Reducing e-waste while securely destroying storage devices requires careful judgment. Minimizing physical destruction is ideal, but for situations such as failed security checks, it becomes necessary. If you do so, it’s important to choose the appropriate destruct method and to rely on vendor-approved equipment to ensure effectiveness and compliance.
In the pursuit of responsible data destruction, best practice is now to avoid outdated techniques like shredding and pulverizing. Instead, use methods such as incineration, melting, and disintegration to align with current standards such as IEEE 2883. Degaussing is also an acceptable option – as long as the magnet is strong enough.
In any event, the significance of maintaining a streamlined workflow cannot be overstated. Regardless of the destructive method, misplacing a drive risks compromising the entire process. Emphasizing the connection between method selection, equipment validation, and workflow management underlines the importance of a thoughtful and comprehensive approach to hard drive destruction.
Get in touch with Horizon for sustainable and secure solutions for your old data storage hardware.











