Clear sanitization techniques are a simple and effective way to sanitize storage devices. A clear technique removes data from all addressable locations, and leaves the storage device in a reusable state.
In today’s digital age, data security is paramount. Sanitization is essential when storage devices become obsolete, unusable, or are reallocated for reuse or resale. Whether you’re destroying, purging, or clearing storage devices, sanitization plays a crucial role in data governance by minimizing the risk of unauthorized exposure, particularly for sensitive information.
This guide explores clear sanitization, one of the three sanitization methods outlined in the IEEE 2883 standards. Clear sanitization is a convenient and efficient approach for routine data erasure.

Related Reading
IEEE 2883 offers a structured approach to storage sanitization through three distinct methods: clear, purge, and destruct.
What is Clear Sanitization?
Released in mid-2022, the IEEE 2883 standard carefully defines terminology surrounding data sanitization, and outlines acceptable techniques. The standard explains sanitization as follows:
The general process of denying access to data from storage media, such that reasonable assurance exists that the data cannot be retrieved or reconstructed.
IEEE 2883, §5.1
“Clear” is a class of sanitization techniques. It is defined as follows:
Sanitize using logical techniques on user data on all addressable storage locations for protection against simple noninvasive data recovery techniques using the same host interface available to the user.
IEEE 2883, §3.1
Clear sanitization techniques differ from purge techniques, which render addressable and nonaddressable storage locations inaccessible to even state-of-the-art laboratory techniques.
What Is Clear Sanitization For?
When it comes to sanitization, the clear method will work in a pinch for routine erasure of low-sensitivity information. Whether you’re a data center ITAM looking to reallocate drives at scale or an individual owner eager to securely dispose of a personal device, clearing a storage device is generally easy and cost effective.
Purge techniques are more secure than clear, and destruct techniques are more secure than purge. However, destruct techniques never leave drives in a reusable state. Purge occupies a balanced center position among the three methods, providing robust security while also allowing for hardware reusability in certain cases. Even when a purge technique makes a drive unusable, it leaves the device sufficiently intact to let one salvage valuable hardware components.
Nonetheless, clear sanitization offers a number of key advantages:
- Ease of Use. By definition, every clear technique can be performed using the same host interface available to the user. Out of clear, purge, and destruct, clear requires the least effort.
- Encouraging Reuse: Clear sanitization leaves drives in a reusable state. This means you can internally repurpose, resell on the secondary market, or donate.
- Widely Applicable: Clear allows you to sanitize older devices that might not support device commands for authorized purge techniques. If your device is broken, clear won’t work—but it’s a good method for most other devices.
Related Reading
The secondary market for properly sanitized HDDs is a key part of a push to make data storage more sustainable. By buying recertified or refurbished drives, you’re reducing e-waste and cutting emissions due to manufacture.
Sanitization Techniques: Overwrite and Block Erase
Clear sanitization techniques do not erase data from nonaddressable locations. These are logical or physical locations on a drive that cannot be read or written using the host interface. When data is rewritten in an SSD, the flash controller actually writes to a different location. This means that advanced techniques may still recover that data at its original physical location. IEEE 2883 gives reallocation pools, overprovisioning, and caches as examples of nonaddressable locations in an SSD (§6.5.1).
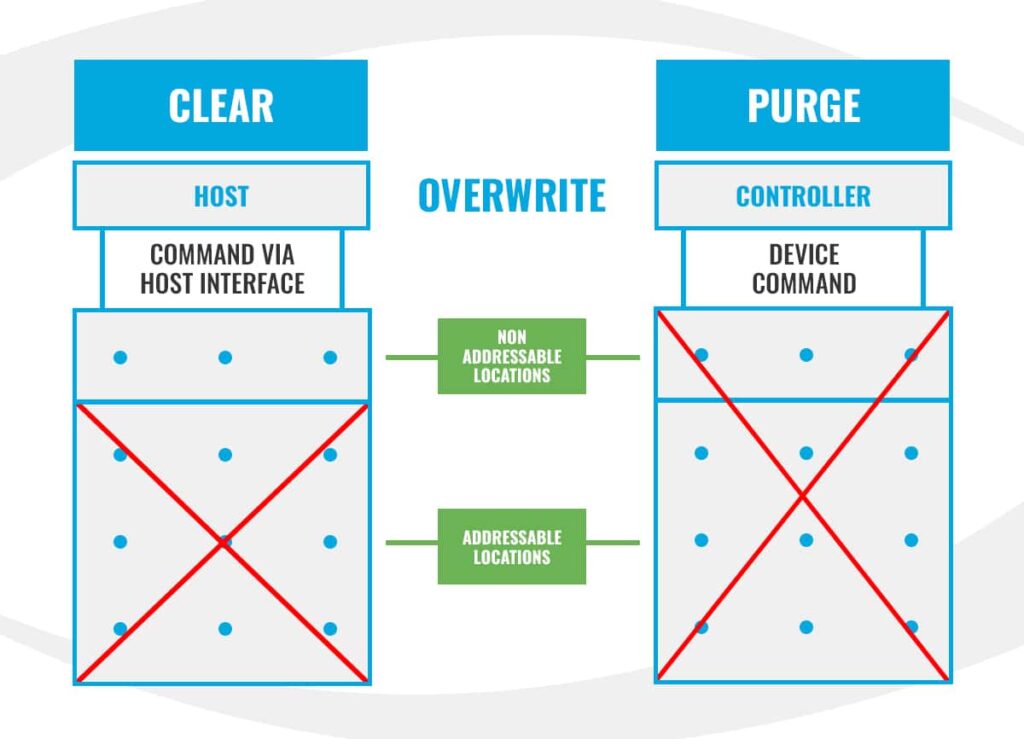
Overwrite: Clear overwrite involves writing data patterns to all addressable locations within electronic media. This process is applicable to most media types, except those like worm tape cartridges that don’t allow for data erase or modification.
Since every addressable location must be overwritten, overwriting tends to be slow. It’s particularly time-consuming for large-capacity storage devices. Furthermore, overwriting may not work when dealing with damaged or non-rewritable storage media.
Block Erase: Clear block erase applies to semiconductor storage media. It’s when a large section of a NAND or other device is electronically dumped in a single operation. This method is faster than overwriting but still may still take a while for high-cap storage devices with many erase blocks.
Like overwrite, block erase can be performed by issuing commands through the host interface itself. Many storage devices have a format or sanitize command that erases all blocks, whether accessible or inaccessible, that could contain user data. Commands to block erase individual blocks are not generally supported. Block erase sanitization is also gentler on NAND storage media compared to repeated overwriting, which can shorten its lifespan (§8.4.1).

Related Reading
While clear or purge is more sustainable, destruct is sometimes necessary for high-sensitivity data or for damaged media.
Verification Of Clear
After sanitizing your drive, it is important to verify that the technique was effective in rendering the data inaccessible. For verification of purge or clear, this check can be performed using the storage device interface itself, and involves confirming the execution of the relevant command (§7.1).
Verification of clear sanitization is done using representative sampling. This is achieved by randomly selecting locations that represent at least 5% of the addressable space or by dividing the storage media into equal-sized subsections and choosing locations from each subsection to ensure adequate coverage.
Clear vs Purge
Executing clear is generally easier than purge. Older drives are also more likely to support clear techniques than rigorous purge techniques. Clear is also the sanitization method most likely to leave drives in a reusable state, and might be a particularly attractive option for internal reuse.
However, there are sometimes reasons to to opt for purge over clear:
- More Comprehensive: In NAND SSDs, purge also sanitizes data in overprovisioned spaces, reallocation pools, and caches, which clear does not.
- More Secure: Purge is more robust and reliable than clear, since purge protects against sophisticated lab-based attacks.
- Sometimes Quicker: Cryptographic erase, a much faster sanitization technique, is only possible through purge. By encrypting the encryption key itself, data can be rendered inaccessible in the blink of an eye.
Resist the temptation to combine multiple clear or purge methods. If done right, once is enough, and layering on multiple sanitization techniques does not enhance security. It can even pose new risks. For example, combining cryptographic erase with a clear technique can significantly slow the sanitization operation and impede the ability to verify the cryptographic erase.

Related Reading
Purge is a more rigorous method of sanitization, which prevents even state-of-the-art laboratory techniques from accessing data from storage devices.
Data Classification: Should You Clear, Purge, or Destruct?
When sanitizing a drive, your choice of sanitization method depends on the data which resides in it, and on your organization’s data security categorization and policies. Factors like environmental concerns and data categorization also play a role in determining whether clear, purge, or destruct methods are favored.
Classifying data can be tricky. It’s also easily neglected, cautioned industry expert Jonmichael Hands in a recent podcast interview. “We see a lot of folks just not properly doing some basic housekeeping on low versus medium versus high business value data”, he explains. “That’s an extremely important prerequisite for how you describe the risk tolerance of customer.”
Hands advises that firms have clear classification policies rather than delegating the task. “I think a lot of these companies are just looking to ITADs to go figure that out, but it’s up to the company to classify.”
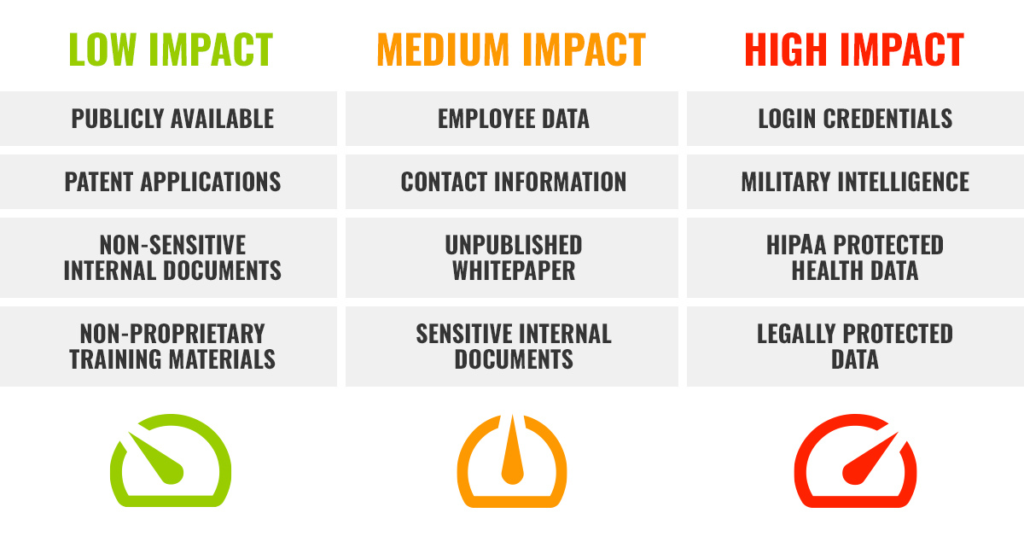
Where to start? IEEE 2883 outlines three broad security classes, each paired with a different sanitization method:
- Low impact (Clear sanitization): Minimal harm if information is disclosed to unauthorized parties.
- Medium impact (Purge sanitization): Moderate consequences if information is disclosed to unauthorized parties.
- High impact (Destruct sanitization): Severe consequences if information is disclosed to unauthorized parties.
Ultimately, your company is the one responsible for determining the threshold for security classification, helping ensure the firm doesn’t violate regulations on data protection.
Clear Sanitization By Storage Type
Detailed in IEEE 2883 standards, the specific instructions for clear sanitization differ between storage interfaces (ATA, SCSI, and NVMe). It’s usually a simple command, or series of commands. It may also involve tinkering with some settings to ensure your command reaches all addressable locations.
Different storage media types, such as hard drives or solid-state drives, may also require specific sanitization methods. IEEE standards also cover sanitization for a wide range of devices, including magnetic media, SSDs, embedded flash, USB, and more. Note that in some cases, clear sanitization commands may involve vendor-specific operations as well.
Clearing Things Up
Clear offers a user-friendly and cost-effective solution for data sanitization, and is particularly suitable for low-sensitivity data or drives which you will repurpose internally. However, it is crucial to understand the limitations of clear, especially regarding nonaddressable locations. Choosing the appropriate sanitization method depends on how the data on a device is classified according to your organizational policies. By following the IEEE 2883 guidelines, organizations can ensure secure data erasure while promoting responsible environmental practices.
Get in touch with Horizon for expert support with every aspect of data sanitization.











